Threat Management: Best practice for your business

In my previous blog articles, I highlighted the most significant cybersecurity threats faced by businesses in 2023 and debunked five prevalent misconceptions surrounding threat management. Moreover, I emphasised that safeguarding against cyber threats demands an ongoing commitment rather than a singular investment. In this concluding blog post, I will outline the best practices to ensure the safety of your business.
Why is Threat Management so important?
Before we go into the best practice of Threat Management, let me explain its importance. The variety of threats has significantly increased and attack strategies have become more complex across the globe. Your Security Operations Centre (SOC) teams must prioritise cybersecurity capabilities and implement a practical Threat Management framework.
If a data breach can be detected sooner the blast radius can be significantly reduced, cutting the financial cost substantially and reducing any fines imposed. According to the data breach report published by IBM in 2022, companies can save more than £960K if they can detect a data breach in 200 days or less.
Therefore, an effective Threat Management plan is essential for your company to have the best chance of quickly detecting and responding to threats.
What’s the best practice for Threat Management?
Threat Management requires seamless integration between people, processes and technology to stay ahead of emerging threats and security risks. Here’s some advice on what you need for each element.
People – Establishing a cybersecurity culture
Your C-suite executives and Board members play a crucial role in establishing a cybersecurity culture. By formulating a governance structure and proactively communicating their expectations to the employees, leaders and managers can motivate them to learn the risks and cooperate with your company’s cybersecurity strategy.
Processes – NIST Cybersecurity Framework
I recommend the NIST Cybersecurity Framework (CSF 1.1) to help you effectively manage the threats. This is a set of guidelines published by the U.S. National Institute of Standards and Technology to mitigate cybersecurity risks for organisations. According to a survey in 2021, almost 48% of respondents said they were using this framework standard to map their control system. Furthermore, NIST will launch a new and more significant update to the Framework, CSF 2.0, in early 2024 to keep pace with technology and threat trends, integrate lessons learned and move the best practice to common practice.
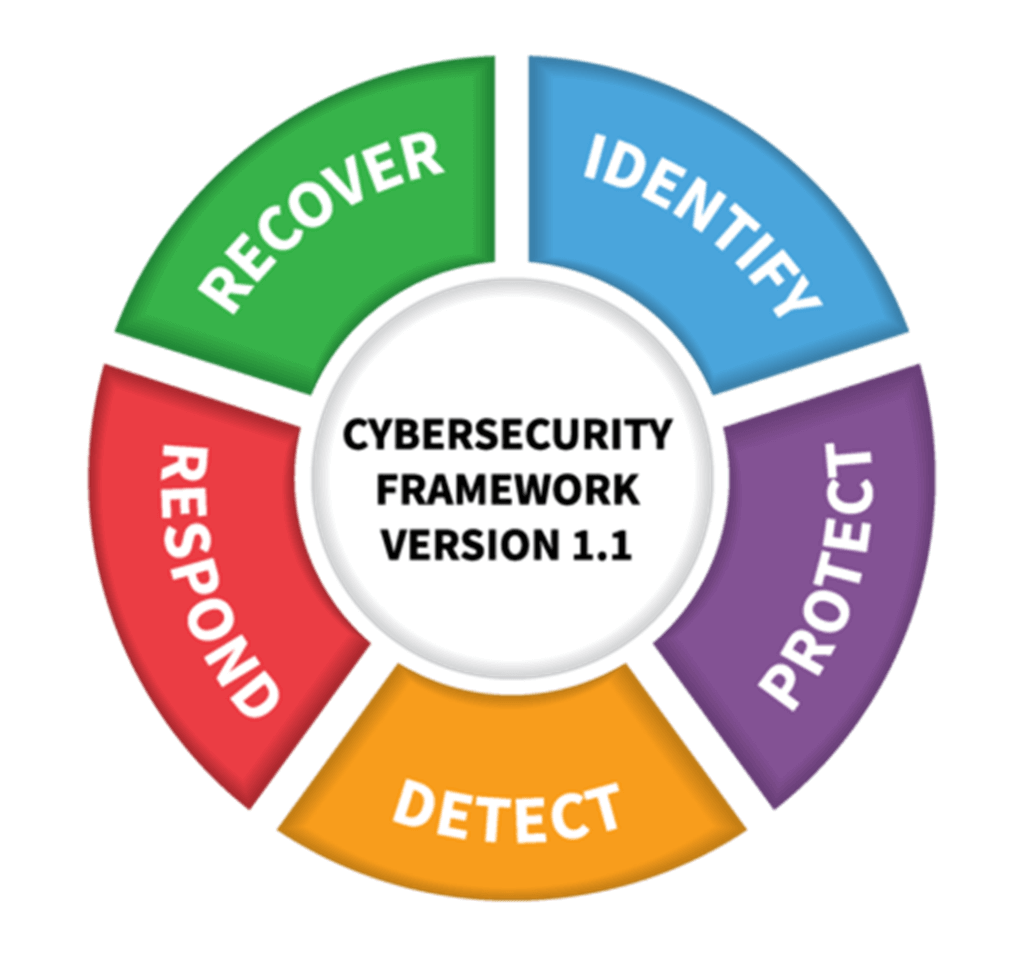
CSF 1.1 comprises five primary functions: Identify, Protect, Detect, Respond and Recover. These functions are not intended to form a sequential path but are performed in parallel, forming an operational culture that addresses the dynamic cybersecurity risk.
Credit: N. Hanacek/NIST
Identify – This is the fundamental function for effectively using the Framework. Your SOC teams should thoroughly understand your business resources and risks. The activity categories include Asset Management, Business Environment, Governance, Risk Assessment and Risk Management Strategy.
Protect – Your SOC teams need to develop and implement appropriate safeguards to ensure the delivery of critical services. This function encompasses activities in Identity Management and Access Control, Awareness and Training, Data Security, Information Protection Processes and Procedures, Maintenance and Protective Technology.
Detect – This function refers to the activities to identify the occurrence of a cybersecurity event on a timely basis. The activities are categorised into Anomalies and Events, Security Continuous Monitoring and Detection Processes.
Respond – Make sure your SOC teams develop an action plan to respond to detected cyberattacks and other cybersecurity incidents. They can create activities around Response Planning, Communications, Analysis, Mitigation and Improvements.
Recover – This is a critical function to ensure business continuity in the event of a cyberattack. Your SOC teams can plan activities in Recovery Planning, Improvements and Communications for cyber resilience plans.
Technology – Leveraging different tools and new technology
Other than the threat management tools that I introduced in the last blog, your SOC teams can leverage various technologies such as Artificial Intelligence, Machine Learning, behavioural analysis, prediction tools and Internet of Things modules to automate parts of the Threat Management process. This can help ensure your data integrity and prevent any holes in your cybersecurity systems.
Conclusion
The success of a comprehensive Threat Management strategy hinges upon the active involvement of all your colleagues, beginning with your organisational leaders. By fostering a robust cybersecurity culture within your company, you can ensure that your colleagues receive thorough training and grasp the significance of cybersecurity. Through the seamless integration of streamlined processes and cutting-edge technology, your company will be able to swiftly identify threats and respond proactively, thereby fortifying information security and bolstering business continuity management.
How CACI can help
CACI has cybersecurity experts who can improve your business’s protection levels. Our capabilities include Zero Trust Network Architecture, Threat Analytics, Systems Hardening and Network Analytics. We can also perform a risk assessment to advise you on your cybersecurity needs. Find out more about our cybersecurity capabilities.
Notes:
[1] Cybersecurity standards usage control systems 2021 | Statista
[2] Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1 (nist.gov)
[3] Quick Start Guide | NIST
[4] Cost of a data breach 2022 | IBM