How do you start implementing Zero Trust Network Architecture?
In my previous blog posts titled “Why do we need Zero Trust?” and “What are the benefits & challenges of implementing ZTNA?,” I discussed the rationale, benefits, and challenges associated with implementing Zero Trust Network Architecture (ZNTA). Now, the question arises: how can we effectively put the Zero Trust Model into action? In this concluding instalment of CACI’s Zero Trust series, I will provide a concise overview of the necessary steps to advance ZTNA implementation.
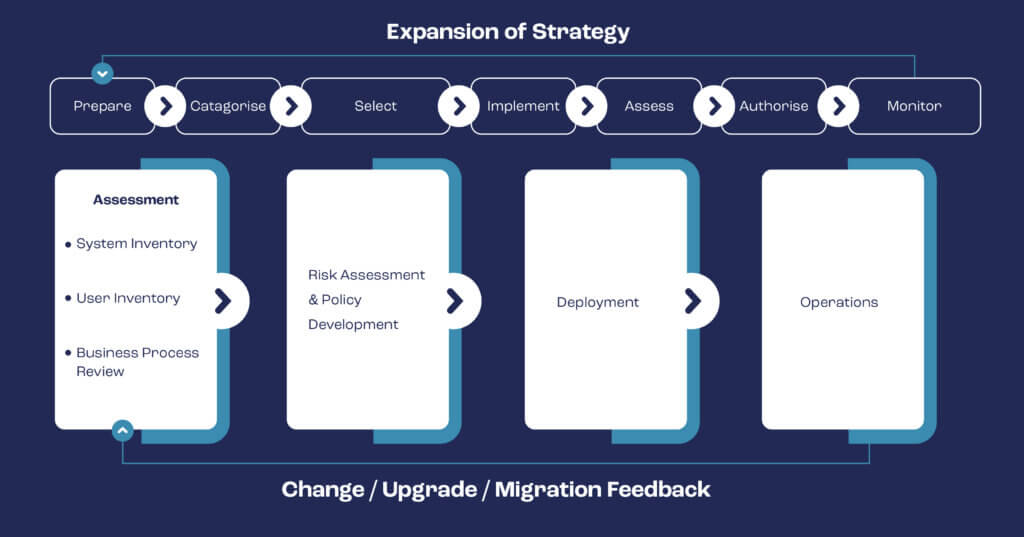
The Zero Trust Network Architecture deployment cycle
Below is a typical deployment cycle as created by the U.S. National Institute of Standards and Technology. Before you bring ZNTA to your company, you need to first assess your system and user inventory and then perform a business process review to understand the current state of your operations.
After creating the initial inventory, you should put in place a regular cycle of maintenance and updating as well as continuing to evaluate your business processes to progressively improve your architecture.
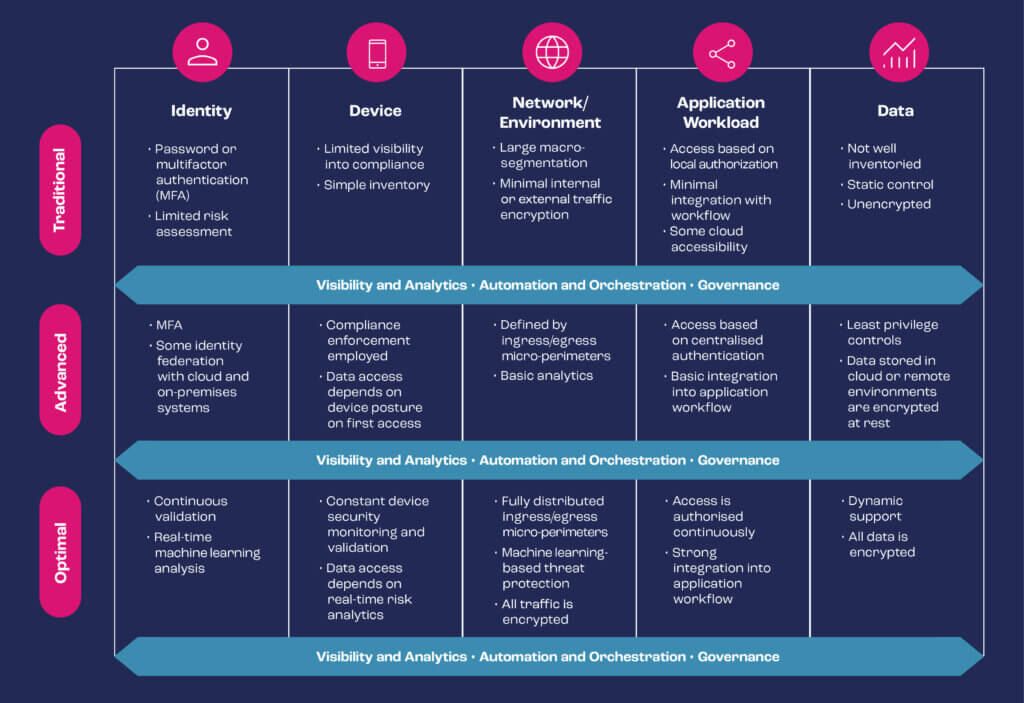
The Zero Trust Maturity Model
As I said in my previous blogs, Zero Trust is a transformative journey and you must invest considerable time and resources to build a mature Zero Trust Network Architecture. The model below shows you a gradient of Zero Trust implementation across five distinct pillars, where minor advancements can be made over time towards optimisation. It can be described using three stages, with increasing levels of protection, detail and complexity of adoption. All these descriptions are used to identify maturity for each Zero Trust technology pillar and to provide consistency across the maturity model:
Traditional – Manual configurations and assignment of attributes; static security policies; pillar-level solutions with coarse dependencies on external systems; least-function established at provisioning; proprietary and inflexible pillars of policy enforcement; manual incident response and mitigation deployment.
Advanced – Some cross-pillar coordination; centralised visibility; centralised identity control; policy enforcement based on cross-pillar inputs and outputs; some incident responses to predefined mitigations; increased detail in dependencies with external systems and some least-privilege changes based on posture assessments.
Optimal – Fully automated assigning of attributes to assets and resources; dynamic policies based on automated/observed triggers; assets have self-enumerating dependencies for dynamic least-privilege access (within thresholds); alignment with open standards for cross-pillar
interoperability; centralised visibility with historian functionality for point-in-time recollection of
state.
Unlike other technologies which are ‘all or nothing’ capabilities, Zero Trust is an extendable spectrum of capability. I know some companies may find it hard to reach the ‘Optimal’ stage because they must invest far more resources than they are comfortable with. Even though their technological capability may be mature enough, their IT team also needs to be upgraded and end-users educated in parallel. Technology and company culture are interdependent.
How CACI can help
CACI has cybersecurity experts who can improve the protection levels of your business. Capabilities include Zero Trust Network Architecture, Threat Analytics, Systems Hardening, Network Analytics and Next Generation Firewalls. We can perform a risk assessment to advise you on what cybersecurity you need.
Together, we can rethink your cybersecurity strategy in this cloud-first world – have you incorporated Zero Trust Model as part of your plan? To build the future of trust from ‘zero’, have a read of our Zero Trust Model whitepaper where we cover everything in this blog series and more. Download your copy now.
Notes:
[1] Zero Trust Network Architecture (nist.gov)
[2] Zero Trust Maturity Model (cisa.gov)