
Cybersecurity breaches are a serious threat to most businesses and can have devastating consequences. A study found that companies typically spent $3.86 million (£2.9 million) per cybersecurity incident.
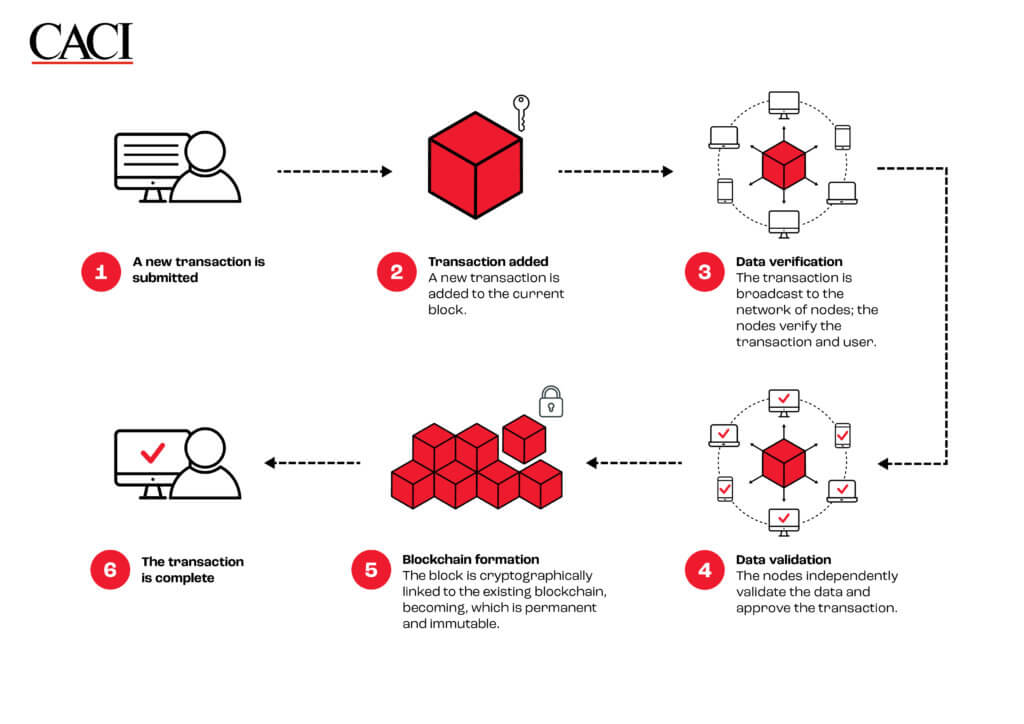
Exploring advanced technology is one of the solutions to reduce your losses in the event of a breach. Blockchain’s features mark a change of era in cybersecurity. We will use the CIA Triad model, a standard model for information security guidance, to highlight some of the features and assess the security level of blockchain. Some business use cases leverage these features to improve their cybersecurity.
CIA Triad Model
The Model represents 3 pillars of Information Security – Confidentiality, Integrity and Availability. This is a valuable model to guide your team in developing security systems.
Confidentiality
Confidentiality means preserving authorised restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information.
- Encrypted data
Blockchain technology can provide high-level security control to assure the confidentiality of data. Even if an attacker can access the blockchain network, fully encrypted blockchain data ensures the attacker cannot read or retrieve information properly. - Public and private keys
Public and private keys are a string of letters and numbers generated by cryptographic algorithms, which are hard to decode by current computing power. They are critical to protecting your user information, the confidentiality of data, authentication and authorisation to the network.
Integrity
Integrity means guarding against improper information modification or destruction and ensuring information non-repudiation and authenticity.
- Cryptographic hashing
Using cryptographic hashing in a decentralised system creates a barrier for any party trying to alter the data. This ascertains the integrity and truthfulness of the data in your system. - Timestamps of data
Transactions in the system are digitally signed with timestamps so that you can trace them back throughout history. - Smart contract
A smart contract is a computer program that automatically executes when specific conditions between buyers and sellers are met. It permits trust transactions and agreements without an intermediary’s involvement. All these transactions are trackable and irreversible.
Availability
Availability means ensuring timely and reliable access to and use of information.
- Decentralised data storage
By storing a complete set of data in a peer-to-peer network, data is still accessible in other nodes if a node is down or attacked. This highly reduces the chance of an IP-based DDoS attack causing operational disruption.
Business use cases in cybersecurity improvement
Lockheed Martin
Lockheed Martin integrates blockchain-based cybersecurity applications into their engineering processes, supply chain risk management and software development efforts.
Ron Bessire, the Vice President of Lockheed Martin Aeronautics Engineering and Technology, believes these new cybersecurity approaches will enhance data integrity, speed problem discovery and mitigation, and reduce the volume of regression testing, which results in reduced schedule risk.
Colorado, the U.S.
In 2017, The Colorado government faced 6-8 million attempted cyberattacks daily. The Colorado Senate passed a bill involving blockchain technology for government record-keeping and cybersecurity. They are confident that the expanded use of blockchains may offer transformative improvements to data security, accountability, transparency and safety across dispersed state departments and jurisdictions.
Barclays Bank
Barclays files two patents that revolve around account security – a blockchain platform which can facilitate cryptocurrency transfers and a private blockchain that streamlines know-your-customer processes (KYC).
They created the “world-first” blockchain platform to handle the documentation to approve fund transactions, which was made through the Society for Worldwide Interbank Financial Telecommunication (Swift). The platform uses smart contracts to track log changes of ownership and payment processes automatically.
The other platform allows the bank to store all customer personal information, verify customer identity and trace their credit history easily in a secure environment.
Philips
Philips calls their blockchain project “verifiable data exchange” – researchers in a network of hospitals and universities can request medical-sensitive data they need for research in the system. User experience revolves around three disciplines: anonymising data, requesting data and fulfilling requests. The system stores a full and immutable trail of how data is used, who has accessed it and who has seen it.
Philips researchers believe the transparent storage of data exchange between the involved parties will create a system of shared risk and responsibility.
Conclusion
While blockchain features continuously evolve in order to strengthen cybersecurity, hacking techniques are ever-developing, creating more and more vicious attacks. For cybersecurity specialists, staying up-to-date with the latest changes is essential. Our next article will examine a number of cyber-attacks coordinated against blockchains.
How CACI can help
Keeping up to date with the latest regulations and cybersecurity trends, our experts can enhance your company’s data management solutions, IT architecture and design, service design, business process service, and cybersecurity.
Get in touch with us today.
Notes:
[1] The cost of a cyber attack in 2021 – IT Governance UK Blog
[2] Executive Summary — NIST SP 1800-26 documentation
[3] Lockheed Martin Contracts Guardtime Federal for Innovative Cyber Technology – Apr 27, 2017
[4] Colorado Passes Bill Advocating Blockchain For Gov’t Data Protection And Cyber Security (cointelegraph.com)
[5] Barclays Seeks Twin Blockchain Patents for Banking Services – CoinDesk
[6] Philips Research Trying to Encourage Healthcare Industry to Utilize Blockchain (newsbtc.com)
[7] Philips will challenge tech giants to bring blockchain to healthcare (thenextweb.com)













 From entering new markets to growing market share, mergers and acquisitions (M&As) can bring big business benefits. However, making the decision to acquire or merge is the easy part of the process. What comes next is likely to bring disruption and difficulty. In research reported by the
From entering new markets to growing market share, mergers and acquisitions (M&As) can bring big business benefits. However, making the decision to acquire or merge is the easy part of the process. What comes next is likely to bring disruption and difficulty. In research reported by the 

